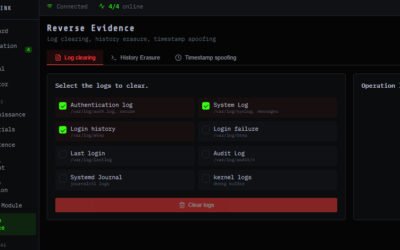
Firewall Flaws, AI-Built Malware, Browser Traps, Critical CVEs & More
Ravie LakshmananJan 26, 2026Hacking News / Cybersecurity Security failures rarely arrive loudly. They slip in through trusted tools, half-fixed problems, and habits people stop questioning. This week’s recap shows that pattern clearly. Attackers are moving faster than defenses, mixing old tricks with new paths. “Patched” no longer means safe, and every day, software keeps becoming…