New Advanced Linux VoidLink Malware Targets Cloud and container Environments
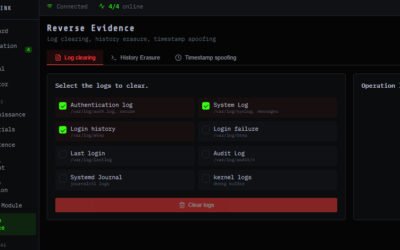
Cybersecurity researchers have disclosed details of a previously undocumented and feature-rich malware framework codenamed VoidLink that’s specifically designed for long-term, stealthy access to Linux-based cloud environments According to a new report from Check Point Research, the cloud-native Linux malware framework comprises an array of custom loaders, implants, rootkits, and modular plugins that enable its operators…

